Q4 '25 Travelers Cyber Threat Report: Attacks on VPNs Drive Ransomware
Q4 2025 saw an unprecedented rise in ransomware attacks, with Qilin leading the charge and VPNs being a prime target for cybercriminals.
We’ve arrived at a “new normal” with more than 300 ransomware leak site victims posted each month. Here’s what you need to know.
Corvus observed 348 new ransomware victims posted to leak sites in October 2023
That represents a 15.12% decrease from September, but a 54.67% increase year-on-year
This is the tenth month in a row with a YoY increase in industry-wide ransomware victims, and the eighth month in a row with victim counts above 300
Despite government takedowns of malware networks, ransomware groups are displaying resilience
In October attacks fell by 15.12% from the prior month according to the volume of victims posted on ransomware leak sites, but remained high from a year-on-year perspective with a 54.67% increase over October 2022. Last month also marked the tenth consecutive with a YoY increase in ransomware victims posted to leak sites, and the eighth consecutive with a count above 300. 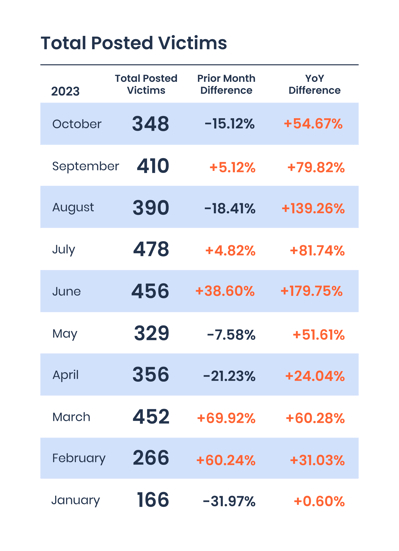
The streak of monthly totals exceeding 300 is particularly significant when you consider that in 2021 — a time that was considered “peak ransomware” — we saw that threshold broken in just three months. In 2022, we didn’t see 300 or more posted in any one month.
That said, a relative slowdown in October was observed across many active ransomware groups. LockBit, ALPHV (BlackCat), Ransomed, and Cactus showed decreased activity from their September levels. After an unprecedented spring and summer in which we saw many ransomware activity records shattered, this may feel like a reprieve — but it’s worth remembering that this was still the highest October on record.
It also bears mentioning for newer readers: the basis for these monthly and quarterly reports is inherently an undercount. Generally, only victims who have refused to pay the ransom or otherwise negotiate a deal with attackers have their data posted on leak sites, so we can always presume a much greater total number of attacks that have been resolved in other ways.
What’s become clear is that despite some month-to-month fluctuations, the lower bound of expected ransomware activity has elevated considerably in 2023. This is further evidence that we are living in a “new normal” of heightened ransomware activity.
.png?width=2405&height=1245&name=Ransomware%20Victims%20by%20Month%20(Oct).png)
Black Basta emerged in 2022 and quickly became one of the most active ransomware groups. Often using Qakbot malware for initial access, the group went quiet for a few weeks this fall after law enforcement took down the Qakbot malware network at the end of August 2023. In October, the group resumed posting victim data on leak sites, showing that the Qakbot takedown had not put an end to their operation. It remains to be seen whether this will continue to slow Black Basta down from their prior levels of activity. They appear to be pivoting to other malware strains as tools for initial access to victim systems.
Overall, we discovered fewer new leak sites in October than we’ve seen over the past several months. One new group we began tracking is “Hunters International.” This group is reportedly using malware highly similar to that of the Hive ransomware gang, which was dismantled by international law enforcement earlier this year. It’s unclear whether this new gang is a rebrand of Hive or merely new operators who obtained access to Hive’s old source code and made some changes. We've seen six victims attributed to this group since discovering its activity on October 20th.
Total Q4 activity was higher than Q3 activity in each of the last two years, so if that is to continue, November and December will be active months
As we pursue our mission to make the world a safer place, Corvus will continue to monitor the threat landscape to protect insureds and contribute to the collective defense of the community.
*Corvus analysis was made possible with supporting data from eCrime.ch. This report is intended for general guidance and informational purposes only. This report is under no circumstances intended to be used or considered as specific insurance or information security advice. This report is not to be considered an objective or independent explanation of the matters contained herein.